For Managed Security Service Providers (MSSPs) and large organizations, managing security across multiple tenants can feel like a frantic juggling act. Constantly switching between different portals, trying to correlate alerts, and enforcing consistent policies is not just inefficient, it’s a recipe for security gaps.
What if you could manage all your tenants from a single, unified command center?
That’s exactly what Microsoft has delivered with its multi-tenant management capabilities in the Microsoft Defender portal. This isn’t just a convenience; it’s a fundamental shift in how security operations can be run at scale. Let’s break down how it works and why it’s a game-changer for your security team.
The Challenge: A Siloed Security Landscape
Traditionally, each Microsoft 365 tenant has its own security portal. For an MSSP managing dozens of clients, this means dozens of logins, dozens of browser tabs, and a fragmented view of the threat landscape. Trying to hunt for a threat that might be targeting multiple clients was a manual, time-consuming nightmare.
This siloed approach leads to:
- Delayed Response: Hopping between tenants slows down investigation and remediation.
- Inconsistent Policies: Ensuring every client has the same, up-to-date security policies is a constant battle.
- Analyst Burnout: The sheer inefficiency of managing multiple portals leads to frustration and mistakes.
The Solution: A Unified Command Center
Microsoft’s multi-tenant management brings all your tenants under one roof. By leveraging technologies like Azure Lighthouse & Microsoft Entra B2B, you can grant your central security team secure, delegated access to manage all your customer or subsidiary tenants from your primary Defender portal.
This provides a single pane of glass for all critical security functions.
Centralized Incident and Case Management
The most immediate benefit is a unified incident queue. Instead of tracking alerts in each tenant, your team sees a single, aggregated list of all incidents and alerts from every tenant you manage.
- Unified View: The incident list includes a “Tenant name” column, so you know exactly where a threat is happening.
- Efficient Triage: You can sort, filter, and prioritize incidents across all tenants at once.
- Case Management: For complex investigations that might involve multiple incidents, you can use the new Cases feature to group related incidents, assign tasks, and manage the entire workflow from one place.
Streamlined Threat Hunting
Proactive threat hunting is one of the most powerful tools in a security team’s arsenal. Multi-tenant management supercharges this by allowing you to run Advanced Hunting queries across all tenants simultaneously.
Imagine you learn about a new indicator of compromise (IOC). Instead of logging into each tenant to search for it, you can write a single Kusto Query Language (KQL) query and run it across your entire multi-tenant environment. This allows you to identify and mitigate threats at scale, instantly.
Consistent Security Policies at Scale
Ensuring every tenant is properly configured is a huge challenge. The multi-tenant portal allows you to create and distribute endpoint security policies from a central location.
- Distribution Profiles: You can group tenants (e.g., by business group or location) and assign specific policies to them.
- Centralized Management: Create and edit policies for antivirus, firewall, and attack surface reduction once, and then deploy them to all relevant tenants.
How to Get Started: A Simplified Guide
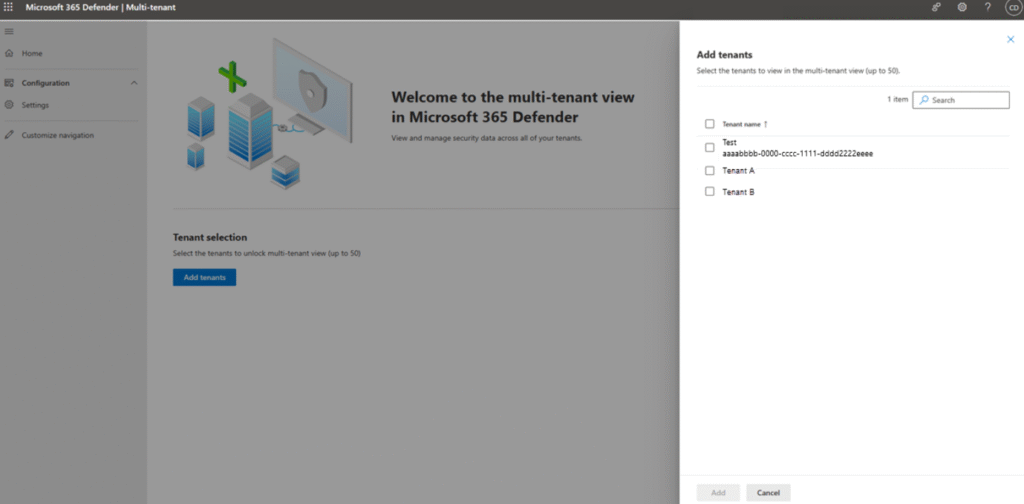
Getting set up with multi-tenant management involves a few key steps:
- Meet the Prerequisites: Ensure you have the right licenses (like Microsoft Defender for Endpoint Plan 2) and permissions. You’ll need to use Azure Lighthouse for managing Microsoft Sentinel data and either Granular Delegated Admin Privileges (GDAP) or Microsoft Entra B2B for Defender data.
- Add Your Tenants: In the Defender portal, navigate to the Settings page for multitenant management and add the tenants you want to manage.
- Configure Permissions with Unified RBAC: Use the Unified role-based access control (RBAC) model to create custom roles and assign permissions to your security team. This ensures that your analysts have the right level of access to each tenant.
- Set Up Email Notifications: Configure email notifications for new incidents to ensure your team is alerted to high-priority threats, regardless of which tenant they originate from.
- Explore the Unified Views: Start leveraging the unified views for devices, identities, and incidents to get a holistic view of your security posture.
The Future of Security is Unified
Microsoft’s investment in a unified SecOps platform is a clear sign of where the industry is heading. For MSSPs and large organizations, the ability to manage security from a single point is no longer a luxury—it’s a necessity. By breaking down the silos between tenants, you can empower your security team to be more efficient, more effective, and ultimately, more successful in defending against advanced threats.
Referebce : https://learn.microsoft.com/en-us/unified-secops/cases-overview


