Managing local domain-joined Windows devices using Microsoft Intune provides organizations with a powerful way to implement modern device management and leverage cloud-based policies, security, and compliance features. This approach is beneficial for organizations that want to continue using their existing on-premises Active Directory while transitioning to cloud management. This blog will walk you through the process of getting started with managing local domain-joined Windows devices using Microsoft Intune, covering prerequisites, configuration steps, and best practices.
Why Manage Local Domain-Joined Devices with Intune?
Managing local domain-joined devices with Intune enables organizations to:
- Implement Hybrid Management: Leverage both on-premises AD and Intune for comprehensive device management.
- Simplify Device Management: Use cloud-based policies for compliance, security, and application management while retaining on-premises configurations.
- Gradual Transition to Modern Management: Gradually move from traditional management approaches, such as Group Policies, to cloud-based management with minimal disruption.
Step-by-Step Guide to Manage Local Domain-Joined Devices Using Intune
Step 1: Configure Azure AD Connect for Hybrid Azure AD Join
Hybrid Azure AD Join allows devices to remain joined to your on-premises Active Directory while being registered with Azure AD. This configuration enables Intune to manage these devices without changing their domain membership.
- Set Up Azure AD Connect:
- Download and install Azure AD Connect on an on-premises server. Azure AD Connect synchronizes your on-premises AD objects (users, groups, and devices) with Azure AD.
- During installation, select the Hybrid Azure AD Join option.
- Configure Hybrid Azure AD Join:
- Open the Azure AD Connect tool.
- Select Configure device options and click Next.
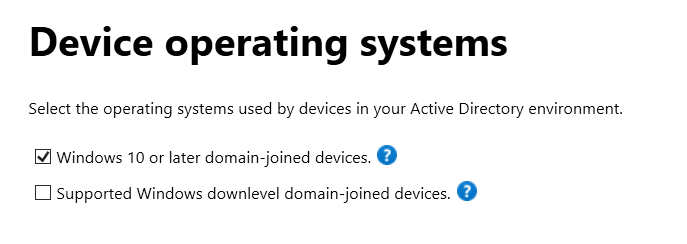
- Choose Configure Hybrid Azure AD Join and select Windows 10 or later domain-joined devices.
- Choose the Azure AD tenant to which devices should be joined and select the Organizational Units (OUs) containing the devices to be managed.
- Verify Synchronization:
- After the configuration is complete, verify that the devices are synchronized and registered in Azure AD.
- Go to the Azure AD portal, navigate to Devices > All Devices, and check that the devices appear as Hybrid Azure AD Joined.
Step 2: Configure Intune for Automatic Enrollment of Hybrid Azure AD Joined Devices
Automatic enrollment ensures that devices registered as Hybrid Azure AD Joined are automatically enrolled in Intune. This step is critical to bring devices under Intune management.
- Enable MDM User Scope in Azure AD:
- Go to the Azure AD portal.
- Navigate to Azure Active Directory > Mobility (MDM and MAM).
- Select Microsoft Intune.
- Set the MDM User Scope to include the users or groups whose devices should be enrolled in Intune (choose either All or Some).
- Save the configuration.
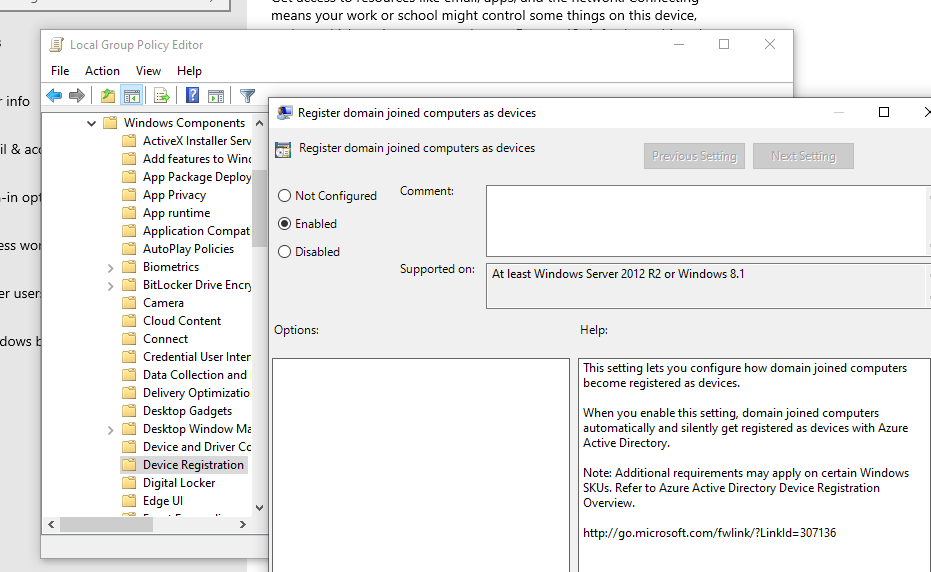
- Configure Automatic Enrollment in Group Policy:
- On your on-premises AD server, open the Group Policy Management Console (gpmc.msc).
- Create a new Group Policy Object (GPO) or edit an existing one.
- Navigate to:Copy code
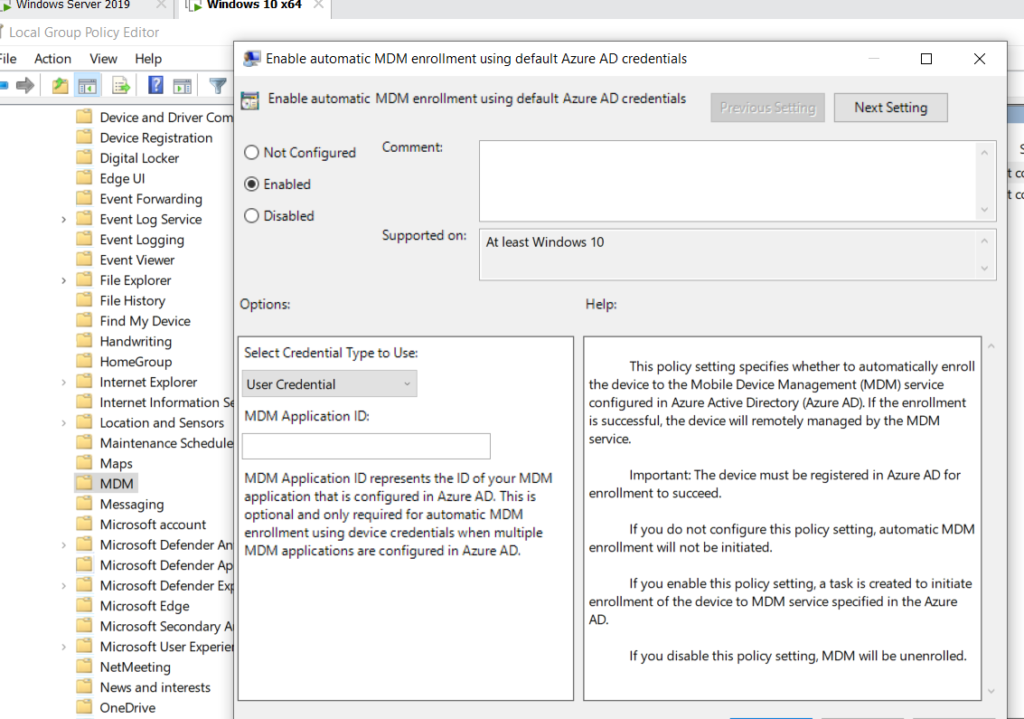
Computer Configuration > Administrative Templates > Windows Components > MDM - Enable the policy Enable automatic MDM enrollment using default Azure AD credentials.
- Configure the MDM enrollment URL:arduinoCopy code
https://enrollment.manage.microsoft.com/EnrollmentServer/Discovery.svc - Link the GPO to the Organizational Units (OUs) containing the devices you want to enroll.
- Verify Automatic Enrollment:
- Restart or ask users to sign out and sign in to their devices to apply the policy and initiate the enrollment process.
- Check the Microsoft Endpoint Manager admin center under Devices > All Devices to confirm that the devices are enrolled in Intune.
Step 3: Assign Intune Licenses to Users
Ensure that all users whose devices are being enrolled in Intune have the necessary Intune or Microsoft 365 licenses assigned.
- Go to the Microsoft 365 Admin Center:
- Go to Users > Active Users.
- Select the users who need to be enrolled in Intune.
- Assign the Appropriate License:
- Assign an Intune license, such as:
- Microsoft 365 E3/E5
- Enterprise Mobility + Security (EMS) E3/E5
- Intune for Education
- Assign an Intune license, such as:
- Verify License Assignment:
- Ensure that each user has a valid Intune license before attempting device enrollment.
Managing local domain-joined devices using Microsoft Intune allows organizations to benefit from cloud-based management capabilities while retaining their existing on-premises AD infrastructure. By following the steps outlined in this guide, you can seamlessly enroll and manage local domain-joined devices in Intune, implement compliance and security policies, and transition to a modern management approach with minimal disruption.
With this setup, you can ensure that your devices are secure, compliant, and centrally managed through Intune, laying the foundation for a smooth transition to cloud-based management in the future.
*** Local domain should be changed to azure domain. ***
Lab 1
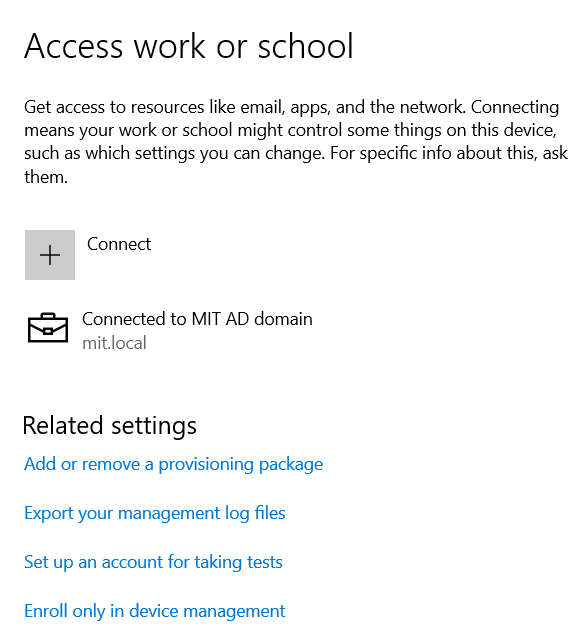
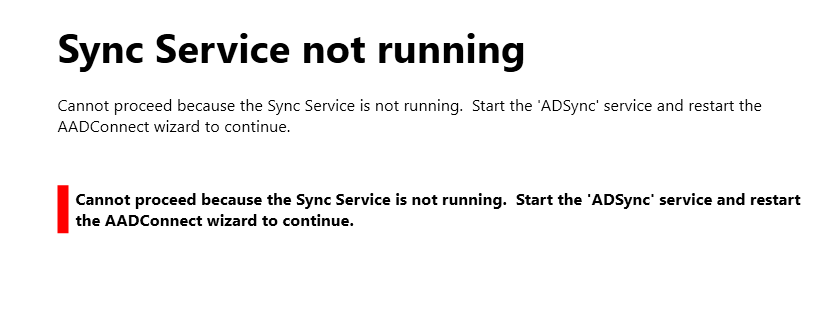
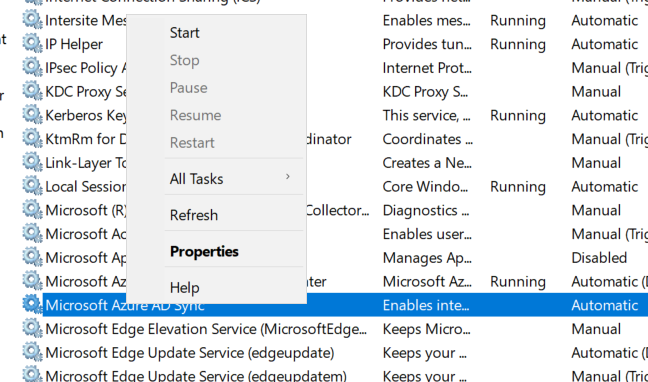
This error occurs while trying to enroll local domain Windows devices into Intune using the Work or School or Company Portal App.
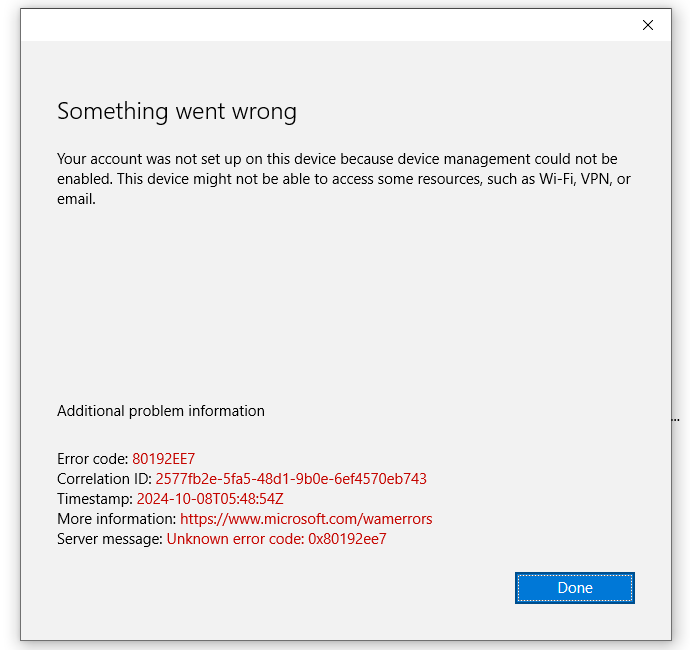
Disjointing from the local domain was not a solution. The Company Portal error disappears when the Workspace One Hub is removed from the registry level, but the Work or School error persists.
Solution : Enroll only in device management.
“https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc”
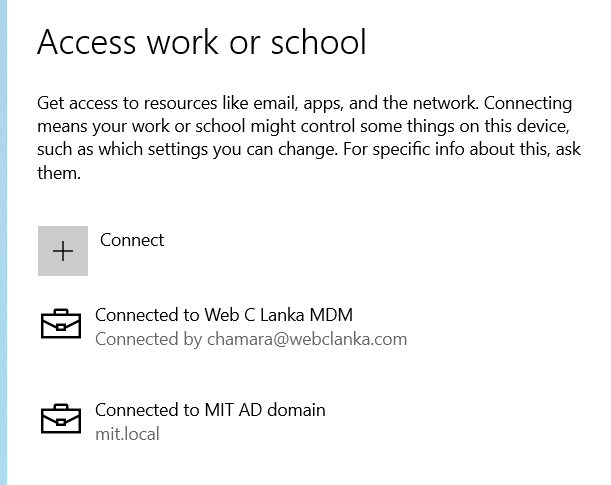
Device enrolling as personal & chnaged it to corporate mannually,
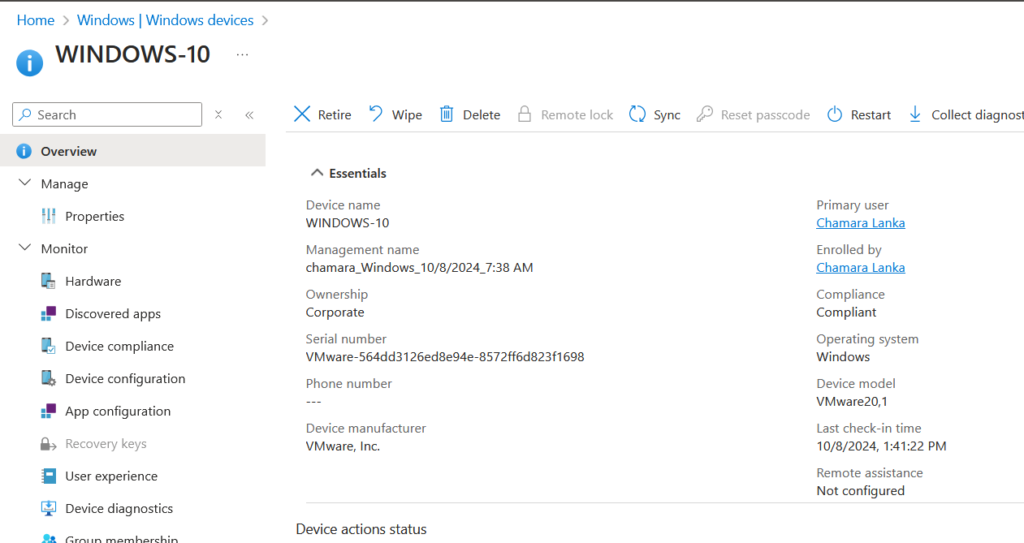
Lab 2

Enrolled to Intune only in device management with Admin account.
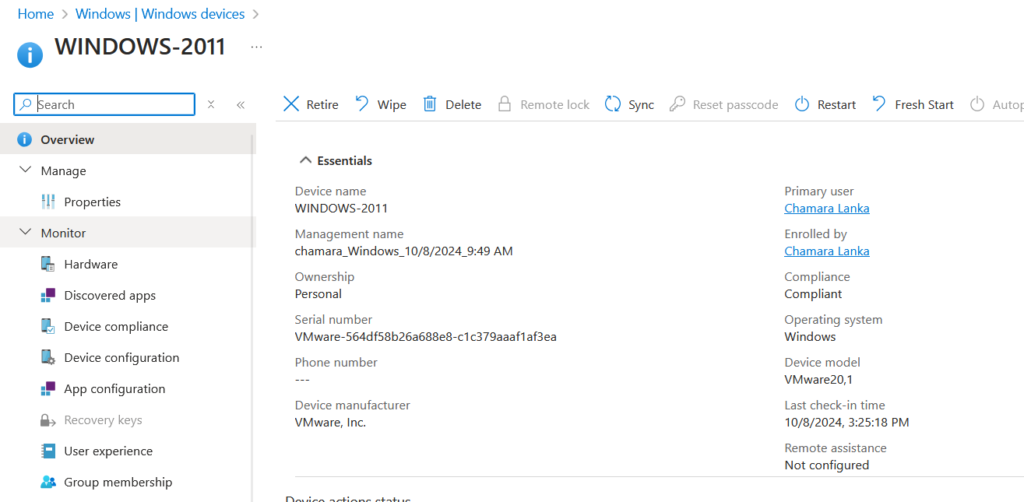
Lab 3
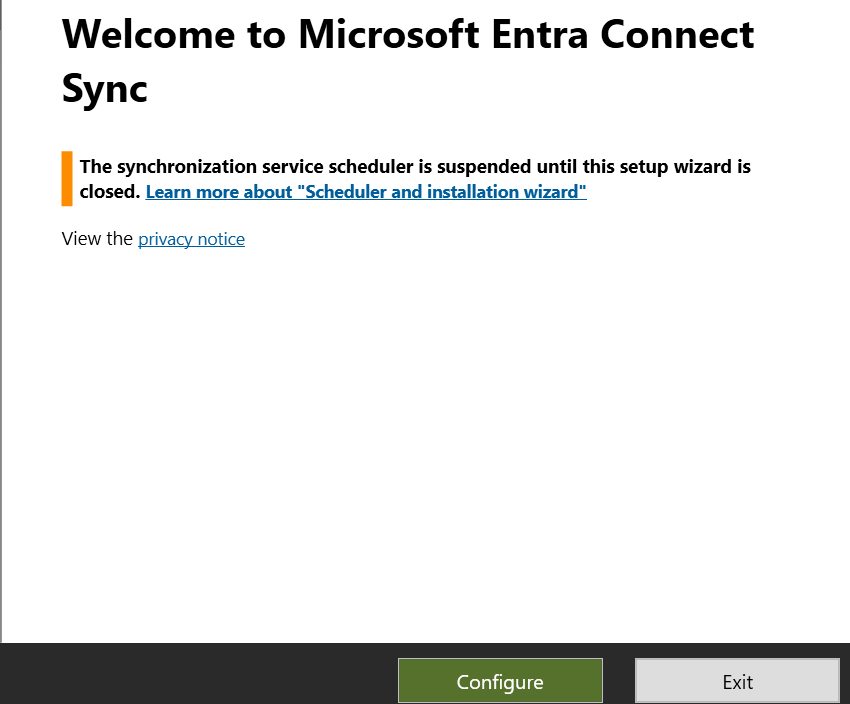
Configure Hybrid Azure AD Join:
Open the Azure AD Connect tool.Select Configure device options and click Next.Choose Configure Hybrid Azure AD Join and select Windows 10 or later domain-joined devices.Choose the Azure AD tenant to which devices should be joined and select the Organizational Units (OUs) containing the devices to be managed.

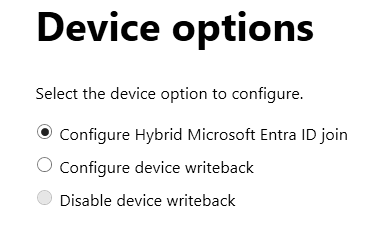
Configure Hybrid Microsoft Entra ID Join (Selected)
- This option is used to enable devices (such as Windows PCs) to be joined to both the on-premises Active Directory and Microsoft Entra ID simultaneously, creating a hybrid environment.
- It allows devices to be managed and authenticated using both on-premises and cloud resources, providing a seamless single sign-on (SSO) experience and enabling features like conditional access and device compliance.
Configure Device Writeback
- When selected, this option enables the writeback of device objects from Microsoft Entra ID back to the on-premises Active Directory.
- Device writeback is useful for scenarios where on-premises applications require information about devices that are registered or joined to Microsoft Entra ID.
Disable Device Writeback
- This option disables any synchronization or writeback of device objects from Microsoft Entra ID to on-premises AD.
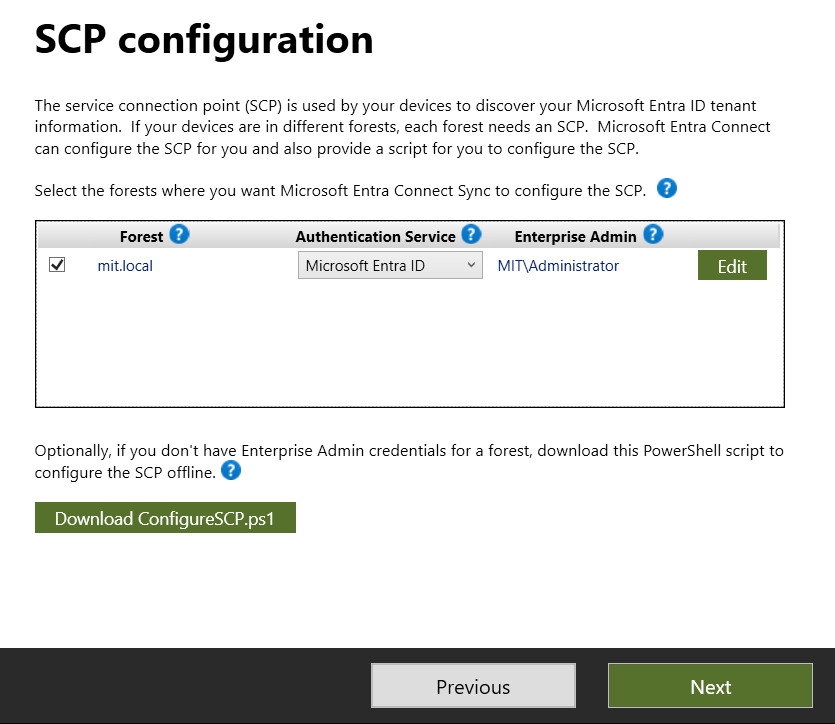
In a hybrid environment, the SCP is used to enable seamless device join and management experiences, such as hybrid Microsoft Entra ID join. It allows devices to discover the cloud endpoint of Microsoft Entra ID, enabling them to join or register without requiring manual intervention.
Check Device Registration Locally:
- On a domain-joined device, open Command Prompt and run the following command:bashCopy code
dsregcmd /status - In the output, check the Device State section for the following fields:
After few minutes >>>

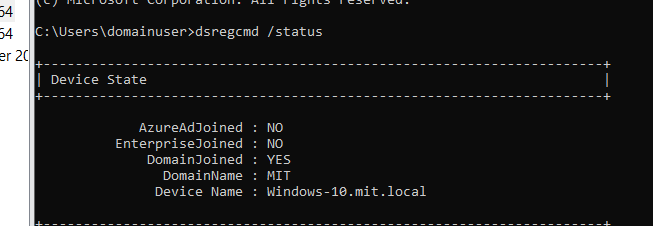
Additional point >>>
After all this add a Intune license for the local domain user from O365 & signed in again.


