DNS (Domain Name System) in Windows Server is a server role that you can install to enable your server to perform as a DNS server.
It serves the fundamental purpose of translating human-friendly domain names like www.example.com into machine-readable IP addresses like 192.168.1.1.
DNS is essential for the functionality of networked services and resources because it resolves easily memorable domain names to IP addresses that network devices need for locating and communicating with each other.
Network Control Panel Applet : ncpa.cpl
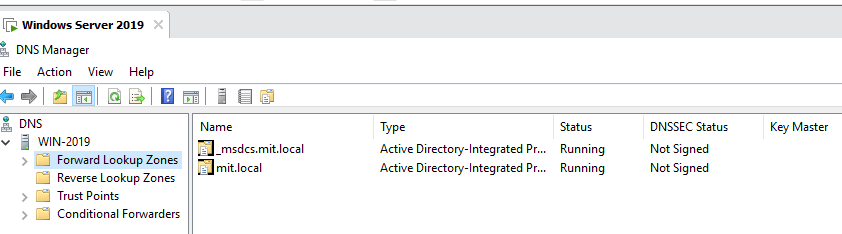
1. Forward Lookup Zones
- Purpose: Translating domain names (like
example.com) into IP addresses which are used by web browsers and other network services. - Content: Within this folder, you will find individual zones for each domain managed by this DNS server. Each zone contains records like A (Address), CNAME (Canonical Name), MX (Mail Exchange), and possibly others that are crucial for network operations.

_msdcs.mit.local
This is a special DNS zone critical for the operation of Active Directory. “_msdcs” stands for Microsoft Domain Controller Services, and this zone contains records that help in locating domain controllers within the domain.
- dc, domains, gc, pdc: These folders under
_msdcscontain various types of service locator (SRV) records and other critical data:- dc: Stores records related to domain controllers.
- domains: Contains GUID-based records for each domain in the forest.
- gc: Global Catalog servers’ records.
- pdc: Primary Domain Controller records.
mit.local
This is the primary DNS zone corresponding to your Active Directory domain name, mit.local. This zone will contain various DNS records necessary for the operation of network services within your domain.
- _sites, DomainDnsZones, ForestDnsZones: These sub-zones/folders organize specific types of records:
- _sites: Contains site-specific SRV records that help in locating services like domain controllers or global catalogs within specific sites of your AD environment. This is useful in larger environments with multiple physical locations.
- DomainDnsZones: Contains DNS records that are specific to the domain
mit.localand replicated across all domain controllers in this domain. - ForestDnsZones: Contains DNS records relevant to the entire forest and replicated to all domain controllers within the forest. This zone typically includes records that are necessary for forest-wide operations and configurations.
Default-First-Site-Name
Under each of the sub-zones like _sites, DomainDnsZones, and ForestDnsZones, you see Default-First-Site-Name, which refers to the default site created when setting up Active Directory. If no custom site structure is defined during AD setup, all domain controllers and resources are initially placed in this site.
- _tcp, _udp: These folders under each site or zone contain specific service records that are used by various protocols:
- _tcp: Contains SRV records related to the TCP protocol, which might include LDAP, Kerberos, and other services.
- _udp: Contains SRV records related to the UDP protocol, typically used for quicker, less reliable communications compared to TCP.
LDAP (Lightweight Directory Access Protocol)
LDAP is used to query and modify items in directory services systems like Microsoft Active Directory, which provide a systematic set of records usually organized in a hierarchal structure. Also for Read and Search Operations & Centralized User Management.
Common Uses of LDAP:
- Authentication and authorization (checking usernames and passwords, checking group membership, etc.)
- Storing information about users (like name, email address, phone number, etc.)
- Managing resources and access control lists.
While LDAP is used for storing and retrieving directory information, Kerberos is used for securely authenticating a user or device’s identity. They are often used together, especially in Microsoft Active Directory environments, where LDAP is used to store all directory information (including user account details and policies), and Kerberos is used to handle authentication of users when they access network resources.
2. Reverse Lookup Zones
- Purpose: These zones do the opposite of what forward lookup zones do. They are used to map IP addresses back to domain names, which is important for services like logging or any service where you want to identify a device by name instead of by its IP address.
- Content: Similar to forward lookup zones but contains PTR (Pointer) records. For example, if you know a device’s IP address and you want to find out what hostname is associated with that IP, the reverse lookup zone provides this information.
3. Trust Points
- Purpose: Trust Points are used within DNSSEC (DNS Security Extensions), which is a suite of extensions to secure the DNS against tampering. Trust Points represent key locations within the DNS hierarchy where cryptographic keys are stored. These keys are used to sign and validate DNS data, helping to protect the integrity and authenticity of DNS responses.
- Content: This folder would contain keys and other DNSSEC-related data for zones that are configured to use DNSSEC. If DNSSEC is not configured, this folder might be empty or minimally used.
4. Conditional Forwarders
- Purpose: Conditional forwarders are used to direct DNS queries for specific domains to specific DNS servers. This is particularly useful in scenarios where you might have multiple internal domains that are managed separately or when integrating with external services that require DNS queries to be directed to specific DNS servers.
- Content: Entries here specify domain names and the corresponding DNS servers to which queries for those domains should be forwarded. For instance, you might set up a conditional forwarder to ensure that all DNS queries for
example-external-service.comare sent to a specific external DNS server provided by the service.


